📌 Introduction
A staggering new cybersecurity breach has just been confirmed: over 16 billion login credentials—including combinations for Apple, Google, Facebook, GitHub, Telegram, and government services—were exposed, marking it as the largest data leak on record this year.
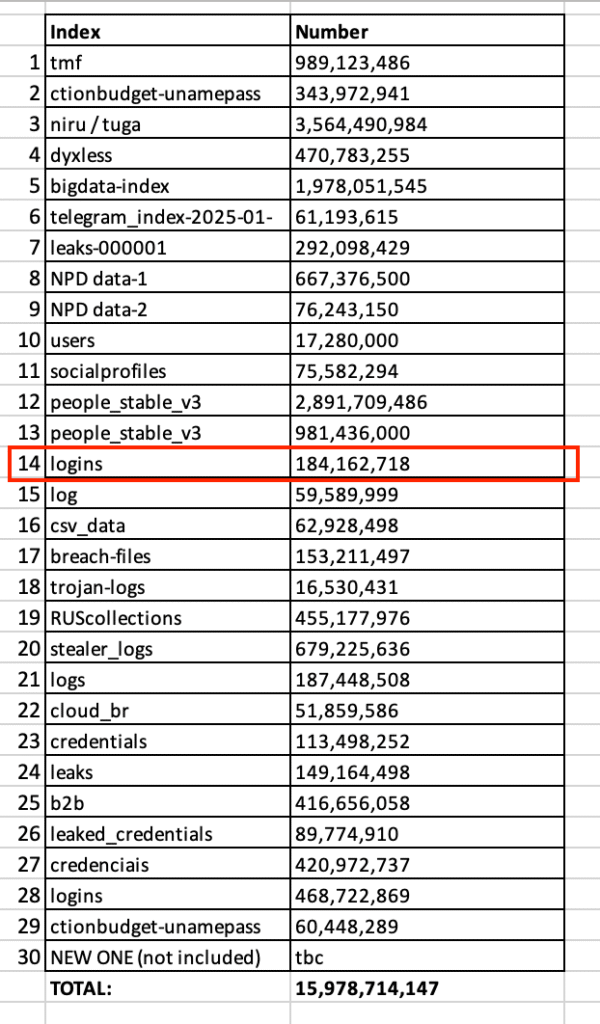
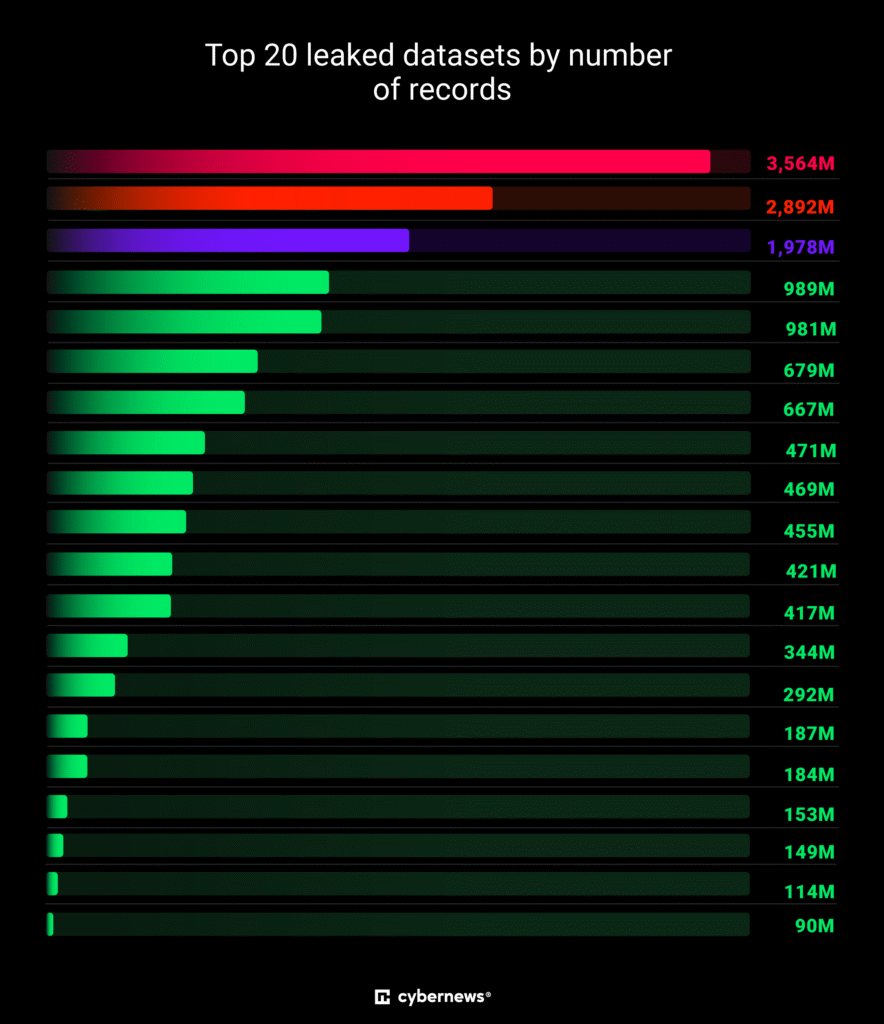
Cybernews researchers discovered 30 different datasets—some containing more than 3.5 billion records each—that are freshly compromised, not recycled from old leaks, making this a highly dangerous trove for malicious actors
🔍 What Records Were Leaked?
- URL, username, password format—ready for automated misuse
- Credential types range across email, social media, VPN, corporate, developer, and government accounts
- Freshly stolen by infostealer malware, making the dataset highly “weaponizable”
📈 Why This Makes History
- Total exposed records: ~16 billion—surpassing any previous leak this year
- Numerous mega-datasets (each up to 3.5 billion records) were briefly—but publicly—accessible
- This isn’t a hack of tech giants—it stems from infostealer malware compromising end-user devices, making it decentralized and unpredictable
- Experts warn that the dataset is a “blueprint for mass exploitation” via credential-stuffing, phishing, identity theft, and account takeovers
⚠️ Who Is Affected & Why It Matters
- Potential risk to any user of social media, email, VPN, crypto, developer platforms, or government sites.
- Duplicate entries mean single accounts may be compromised multiple times, but exact counts can’t be determined
- AI‑driven password‑replay attacks could amplify risk, especially where users reuse credentials across sites.
🛡️ Expert Recommendations
- Change passwords immediately on all accounts—prioritize high-risk ones like banking and email
- Enable strong two‑factor authentication (2FA), especially using app-based or hardware tokens
- Switch to passkeys or biometrics where available; they’re phishing‑resistant
- Use reputable password managers to generate and store strong, unique credentials
- Install anti‑malware tools to detect and remove infostealer viruses
🏢 Platforms & Government Response
Google has strongly urged users to transition to passkeys and enhanced 2FA, emphasizing biometrics and secure device-based authentication for Gmail, YouTube, and beyond
The FBI and CISA are monitoring the breach and broadcasting public warnings against phishing links and password reuse
Cybersecurity firms like Aid: “Organizations must adopt zero‑trust architectures and regularly scan for exposed credentials online.”
🔍 How It Compares to Past Breaches
- 2019 Collection #1 leak: ~2.7 billion records
- 2024 National Public Data breach: ~2.9 billion records (incl. SSNs)
- 2024 Mother of All Breaches: ~26 billion records (mostly older leaks)
- This new 16 billion‑record breach is unique: fresh, in-use credentials collected via malware, making it the most dangerous to date.
🌍 Global Reaction from Tech Giants
As news of the 16 billion-password breach spread, major tech firms responded swiftly to reassure users and update security guidelines:
- Apple released a statement urging users to verify recent account activity via their Apple ID dashboard and switch to biometric logins when possible.
- Google pushed updates for Chrome’s built-in password manager, alerting users about any compromised credentials and encouraging the use of Passkeys and 2-Step Verification.
- Meta (Facebook & Instagram) advised users to log out of all sessions and reset security questions and backup emails.
- Microsoft updated its “Security Copilot” AI to detect large-scale credential reuse attempts on enterprise accounts using Azure AD.
Many platforms began issuing proactive password-reset prompts to suspiciously reused email addresses found in the leaked datasets.
🧪 How Infostealer Malware Collects Your Credentials
This breach wasn’t caused by a traditional hack of big companies. Instead, it stemmed from widespread use of “infostealer” malware, a silent but devastating tool used by cybercriminals to extract credentials from infected devices.
Here’s how it works:
- The user unknowingly installs malware via a fake app, phishing link, or cracked software.
- The malware quietly scans the device’s browser history, cookies, saved logins, autofill fields, and sometimes even screenshots.
- It sends the stolen information to the attacker’s server, often within seconds.
- The credentials are bundled into huge “logs” and resold or dumped on the dark web.
Many of the stolen credentials come from ordinary users—not celebrities or CEOs—which makes the attack more widespread and difficult to trace.
💣 The Danger of Massive Credential Dumps
This isn’t just about your Facebook account. Here’s what can happen when credentials are leaked in this quantity:
- Credential Stuffing: Hackers test your email/password combo on thousands of services to hijack accounts where you reused the same password.
- Phishing Personalization: Using leaked info (location, name, usernames), attackers craft targeted phishing emails that appear 100% real.
- Session Hijacking: Infostealers also grab cookies and tokens, which can let hackers log into your accounts without passwords.
- Ransom Attacks: If corporate accounts are exposed, ransomware groups may lock internal systems until a payment is made.
Even if you’re not the direct target, your compromised account could be used as a stepping stone in larger attacks.
🏢 Corporate Security Checklist
Businesses—especially SMBs and startups—must act fast. If you manage teams, employees, or clients, here’s a 10-step action plan to minimize damage:
- Audit all employee credentials using breach-checking tools like Have I Been Pwned or SpyCloud.
- Enforce password changes across all critical internal systems (email, admin panels, CRM, cloud services).
- Deploy endpoint detection and response (EDR) to monitor for signs of infostealers or keyloggers.
- Train employees to identify phishing emails and spoofed login screens.
- Disable unused accounts and devices that could be silently compromised.
- Enable multi-factor authentication (MFA) on every login point.
- Monitor traffic logs for sudden login attempts from foreign IPs.
- Segment your network to prevent lateral movement by attackers.
- Use password managers with zero-knowledge architecture.
- Prepare a response plan in case of confirmed compromise.
🧠 Expert Opinions & Long-Term Outlook
“This breach isn’t just another database dump. It’s a strategic gold mine for hackers who rely on human laziness—like reusing passwords or clicking sketchy links.”
— Sarah Lin, CISO at RedTeamX
“With the rise of AI-powered credential attacks, the only way forward is to adopt passwordless authentication—biometrics, passkeys, and zero-trust architecture.”
— Dr. Michael Tannen, Cyber Policy Advisor, U.S. Department of Homeland Security
Security experts widely agree that this incident is a wake-up call. The future of access control must lean toward identity verification models that don’t rely on static credentials.
🧼 Everyday Digital Hygiene Tips
Protect yourself even if you haven’t seen your email listed in a breach:
- Never reuse passwords between accounts.
- Install anti-malware and update your OS/software weekly.
- Use app-based 2FA like Google Authenticator or Microsoft Authenticator.
- Be suspicious of any email asking you to “verify” something.
- Regularly check if your data appears in breach monitoring tools.
📣 Stay Updated & Protected
Subscribe to our weekly cybersecurity digest for breaking alerts, password leak updates, infostealer malware insights, and protection tips. Sign up now and take control of your digital safety.
❓ FAQs
Q: Does this mean Apple, Google or Facebook themselves were hacked?
A: No—the breach stems from stolen credentials via infostealer malware on end-user devices, not a compromise of corporate servers
Q: How many distinct users are affected?
A: Impossible to know. Overlapping entries mean single users may appear multiple times across the 30 datasets
Q: Will enabling 2FA stop this?
A: Not fully—infostealer malware can sometimes steal session cookies too. But strong 2FA (app- or hardware-based) greatly reduces threat
📊 Final Thoughts
This record-breaking breach has changed the threat landscape in 2025. With over 16 billion fresh credentials now circulating, both users and businesses must act urgently to secure accounts, update practices, and move away from password-only authentication.
The next cyberattack could begin with your Netflix login—and end with stolen funds or company-wide compromise. Stay alert. Stay informed. Stay secure.
This 16 billion‑record credential dump is a stark reminder: our login practices are deeply flawed. Even passwords assumed to be “old” or “unused” can be weaponized when aggregated at scale.
Users and organizations must treat password leaks as inevitable, responding with swift protection measures and a long-term security stance centered on zero‑trust, passkeys, and continuous monitoring.
📣 Stay Secure & Informed
Don’t wait for an account takeover—change your passwords today, enable strong authentication, and protect your digital presence. Subscribe to our newsletter for real-time cybersecurity alerts, guides, and best practices.

